PCI 30 seconds newsletter #14 – The World Isn't Perfect
The term "vulnerabilities" is often used in the PCI DSS standard to mean the following (per the definition given by the Council):
Flaws or weaknesses which, if exploited, may result in an intentional or unintentional compromise of a system.
Let’s illustrate this by taking our body and soul as the system.
Examples:
- As a first example, imagine that I’m standing in front of you holding in my hand a test tube containing an explosive
product. I warn you to move carefully because this product is movement sensitive. Ahh I can see the fear in your eyes... Suddenly I shake my hand…nothing happens. I explain to you that for this product to be so reactive one needs to add a drop of a reagent. Now let’s imagine that while I’m taking to you someone does so behind my back. What would have happened when I shook the test tube? …Yes, indeed…Sorry, it wasn’t my fault! - As a second example, let’s analyze the following scenario: A car fatally hits you while you are quietly crossing the street. Here you are the system. What could have caused this awful scenario? Bad luck maybe? There are multiple factors that could have lead to this scenario. You simply crossed without paying attention; you had your iPod on; the car driver didn’t see you, you had a bad day and you were deep in thought; you are blind, deaf or both. The environment is also playing a role: Crossing a city boulevard during the peak hours is quite different to crossing a country street on a Sunday morning. The factors above are the weaknesses or vulnerabilities that increase the probability of occurrence of this scenario.
Vulnerabilities in information systems
The world isn’t perfect and certainly not as pertains to information technology. There are a variety of vulnerabilities across information systems - including computers, network systems, operating systems, and software applications – that may originated from vendors, system administration activities, or user activities:
-
Vendor-originated: this includes software bugs, vulnerable services, insecure default configurations, and web application vulnerabilities.
-
System administration-originated: this includes incorrect or unauthorised system configuration changes, lack of password protection policies.
-
User-originated: this includes sharing directories, opening infected documents, selecting easy guessing password, downloading and installing third party software.
Why aren't bugs fixed before software release?
Bugs are a consequence of the nature of human factors in the programming task. They arise from oversights or mutual misunderstandings made by a software team during specification, design, coding, data entry and documentation.
As computer programs grow more complex, bugs become more common and difficult to fix. Often programmers spend more time and effort finding and fixing bugs than writing new code support. On some projects, more resources can be spent on testing than in developing the program.
There are various reasons for not fixing bugs:
-
The developers often don't have time or it is not economical to fix all non-severe bugs.
-
The bug could be fixed in a new version.
-
The changes to the code required to fix the bug could be large, expensive, or delay finishing the project.
-
Even seemingly simple fixes bring the chance of introducing new unknown bugs into the system.
-
It's "not a bug". A misunderstanding has arisen between expected and provided behavior.
Given the above, it is often considered impossible to write completely bug-free software of any real complexity. As a consequence software is released with known or unknown bugs.
Is it a problem? Well let’s see in our next newsletter.
Questions:
-
Did you find this article useful?
-
What is your feeling about the amount of buggy software on the field?
Something is rotten in my kingdom
Ten years ago, self-regulation through the implementation of good security practices was thought to be the way organizations would protect their, and our, sensitive data but the number of reported security incidents demonstrates that self-regulation doesn't actually work. It's like hoping that a kid does his home work only because he fully understands all the benefit for himself. Actually, this kind of self-governing behaviour requires some level of maturity and a deep self-consciousness of the risks faced.
The use of compliance to improve security
When self-regulation doesn't work, the stick is not far away. As a result, the upsurge in the number of contractual and legal obligations in the form of compliance programs imposed to organizations in their respective business sectors.
As a consequence, nowadays compliance is a fact of life. Companies strain under requirements from state privacy laws, healthcare laws, industry regulations and all manner of contractual agreements with customers and partners. These rules and regulations often require organizations to protect sensitive data from threats to confidentiality, integrity or availability. They may also demand that organizations maintain uptime, recover from losses, monitor use, and undergo audits.
While compliance may require some understanding of security, it has as much to do with governance, process and documentation as it does with technology. Furthermore compliance responsibility is often spread among the legal department, privacy officers, audit, human resources and, of course, IT security.
Facing the threat of financial penalties, legal proceedings or business disruption, companies unwillingly embark on this compliance journey. Unfortunately the consequences in terms of security aren't really positive. For the board, the objectives of compliance and security are very distant. Some companies reallocated the already small security budget to the compliance project and focus this budget and their resources on achieving compliance in the shortest (and cheapest) possible way.
Obviously companies do not comprehend, or do not want to comprehend, the underlying message behind compliance. Self-regulation doesn't work and the stick doesn't really help. Security remains the poor stepchild.
One must rethink about the problem. So let's step back and look at this question from another perspective: can we envisage a way to improve security through compliance? Probably, but we need to open our eyes and get creative. I would like to discuss this more with you so I've started a community group for this purpose. So please join the Compliance Paradigm group and let's talk.
Didier
Debating Cyber Warfare - Questions from .GOV
The NCDI
A few months ago I was engaged by a friend who had desires of starting a new foundation in the Netherlands. He surmised that the Dutch Ministry of Defence could use some help in establishing proper Cyber Doctrine. Now, a scant 6 months later, we find our group is firmly set at 7 people and the foundation has officially been established. It is called the Dutch Institute for Cyber Doctrine (NCDI) and I sincerely hope you will hear more of us in the near future.
 I mention the birth of this foundation because through some proper networking we've been asked for input by our government with relation to Cyber Warfare. The request for information contained such interesting questions that I felt I could almost dedicate an entire article on each question, and so I did. I hope to generate some really interesting debates with these questions. Without further ado, here is the first question:
I mention the birth of this foundation because through some proper networking we've been asked for input by our government with relation to Cyber Warfare. The request for information contained such interesting questions that I felt I could almost dedicate an entire article on each question, and so I did. I hope to generate some really interesting debates with these questions. Without further ado, here is the first question:
"After Land, Air, Sea and Space, Cyberspace is generally considered to be the fifth warfighting domain. Based on what political and military objectives can operational cyber capabilities be developed and deployed? Please define the nature and role of operational cyber capabilities during military operations."
An Answer
While you'll find a plethora of discussions in which it is still hotly debated what it all means, it is very likely that future conflicts will not be 'pure cyber wars' in the same way we haven’t seen ‘pure nuclear wars’ or ‘pure air wars’. Instead it is much more likely that new conflicts will contain cyber attacks or cyber espionage as part of a larger strategic plan. In fact we've already seen it in conflicts as early as the war in the Persian Gulf in 1991, where the famous and recently deceased Robert Morris was said to have launched the first US cyber attack. Many people now ask the question what the political and military impact is of cyber warfare, and this is a very valid question. However, it should not be confused with political and/or military motive, because nothing has really changed in that regard. War is, as Clausewitz said, the continuation of Policy through other means, and that is exactly what cyber is: just another means.
With that in mind, I feel the first half of the question is somewhat flawed. Political objectives are not usually fundamentally changed by technology, though military objectives certainly can be, and with the advent of cyber warfare it is easy to confuse or even conflate the two. So for me, the question is really “What military objectives should be the focus of operational cyber capability development?”.
The answer to this question will probably always remain difficult to answer, because the technology surrounding cyberspace is continually changing. Furthermore we find that the application of said technology is ever changing as well, making it very hard to pin down exactly if and where there are any fixed strategic points or objectives to aim exploitation development to. What is a sensible and effective angle today may be completely obsolete tomorrow. Based on what we’ve seen so far (of what we’ve been allowed to see, that is), we can assume that in the foreseeable future, cyber attacks will not have a directly kinetic component. That is to say – cyber attacks don’t (and won’t) act like bullets, bombs or missiles. As we know and understand it now, it can be used as a strictly supporting function to ongoing operations. The key word here is Information – its discovery, manipulation or denial. Cyber attacks could be succesfully applied to disable a radar array preventing a strategic bombing or insertion, or more locally to disable alarm systems on a house that needs to be breached quietly. It could (and already is) be used highly effectively to break into the networks of defence contractors and steal the highly sensitive specs of enemy technology, and in turn use that information to render them harmless to your troops. Interestingly enough, you could also use it the other way around: To make your enemies see things that aren’t there, such as by flooding their radar screen with bogus information or by infiltrating and corrupting their chain of command’s methods of communication. Whatever the application, it is important to note that virtually all these attacks are of a temporary nature. They don’t really change things permanently. As such, you should not depend on cyber attacks to give you a lasting advantage. It is highly likely that the target will, at one point, discover the attack and take steps to undo it.
The bottom line is that before being able to develop operational cyber capabilities, it is important that you understand the nature of Cyber attacks. What it is, and what it isn’t. You won’t win any wars with Cyber alone, but you may be able to increase the success rate of your missions and give your opponents a very frustrating time during ongoing operations by applying this exciting new technology.
About the author: Don Eijndhoven has a BA in Informatics (System & Network Engineering) with a Minor in Information Security from the Hogeschool van Amsterdam, The Netherlands. Among a long list of professional certifications he obtained are the titles CISSP, Certified Ethical Hacker, MCITPro and MCSE. He has over a decade of professional experience in designing and securing IT infrastructures. He is the CEO of Argent Consulting and often works as a management consultant or Infrastructure/Security architect. In his spare time he is a public speaker, works as a Project Manager for CSFI and acts as its Director of Educational Affairs in the EU region. He also blogs for several tech-focused websites about the state of Cyber Security and is a founding member of Netherlands Cyber Doctrine Institute (NCDI), a Dutch foundation that aims to support the Dutch Ministry of Defense in writing proper Cyber Doctrine.
Cross-posted from ArgentConsulting.nl
Should You Store Passwords In The Cloud?
It seems that almost every site on the web requires a password. At least twice a week, I get an email from someone who wants me to join yet another network, which requires yet another username and password. You can cop out and use the same username and password combination, but that’s just asking for trouble.
The key to surviving password management going forward is to make a small investment in a password management service that stores your passwords in the cloud and also on your computer. The best thing about a password manager is that you ultimately have just the one master password to remember, which gets you access to all the different passwords for each site.
What to look for:
- A password generator tool that makes strong passwords that cannot be cracked, and that you never really need to remember, because they are all stored in the password manager.
- One that works across multiple browsers and can sync multiple PCs.
- Smartphone application syncing with the cloud.
- Security of password managers is pretty much a nonissue at this point, since most have levels of encryption that can’t be easily cracked.
The real security vulnerability is with your own computer and any existing or future malware that can log your keystrokes or take screenshots. Run virus scans and the most updated version of your antivirus software to prevent any infections.
Another layer of protection is to add your computer’s built-in onscreen keyboard to your task bar and use it to enter your master password.
Cloud-based password managers:
RoboForm is my favorite. It’s $9.95 for the first year and $19.95 every year after that.
Install RoboForm on as many computers and mobile devices as you wish, all with the same license. Seamlessly keep your passwords and other data in sync. Always have a backup copy of your passwords and other information. It’s also extremely secure and easy to use.
Keepass is free. This is a free open-source password manager, which helps to securely manage your passwords. You can store all your passwords in one database, which is locked with one master key or a key file. So you only have to remember one single master password or select the key file to unlock the whole database. The databases are encrypted using the best and most secure encryption algorithms currently known (AES and Twofish). For more information, see their features page.
For $39.35, 1Password can create strong, unique passwords, remember them, and restore them, all directly in your web browser.
LastPass is also another good free option.
Using a password management tool like those listed above is easier: never forget a password again and log into your sites with a single mouse click.
It’s everywhere: the program automatically synchronizes your password data, so you can access it from anywhere at anytime.
It’s safer: protect yourself from phishing scams, online fraud, and malware.
It’s secure: all of your data is encrypted locally on your PC, so only you can unlock it.
Robert Siciliano, personal security expert contributor to Just Ask Gemalto.
Top Six Free Cloud Storage Centers
“Free” is one of my favorite words so when I have the option to get something for free, I will allocate a reasonable amount of time figuring out how I can apply that to my life before I determine if I should adopt it, or if it’s worth the extra few bucks for the paid version, or if it isn’t worth my time at all.
Backing up data is as important as securing your data, so I back up in multiple places, some of which are free and some that charge a fee.
Here are the freebies:
Google: For Windows, Mac, iOS. Up to 10 GB free space. Designed to store documents in Google Docs, photos in Picasa. Google storage is scattered. It’s only effective for documents and photos.
iCloud: For Mac, iOS, limited functions for Windows. 5 GB free space. Designed to automatically back up all your Apple devices wirelessly.
Amazon Cloud Drive: For Windows, all Adobe Flash enabled devices, not for iOS. 5 GB free space, then $1 per extra GB. Designed for manual upload and backing up media.
Windows Live: For Windows, Mac. 25 GB free space. Designed to store anything you want.
Dropbox: For Windows, Mac, iOS. 2 GB free space, then $2 per extra GB. Designed to store anything you want. It’s the only cloud storage that seamlessly and automatically syncs all your devices in one place.
YouSendIt: For Windows, Mac, iOS. 2 GB free space. Designed to store anything you want. Allows for sending links via email for downloading.
Each of the above cloud storage spaces fits a certain need based on the systems and devices you have. If all you need is a data dump, then Windows Live is it. If you need synchronicity across platforms, go for Dropbox. If you are all Apple, then iCloud is your service. YouSendit is the only one that allows for emailable links to download files, which I use a lot.
Robert Siciliano, personal security expert contributor to Just Ask Gemalto.
IT GRC Professionals Needed
Fishnet Security, one of the US most trusted information security organizations, is interested in discussing employment opportunities with ITGRC professionals throughout the US.
Specifically, Experience with the RSA Archer ITGRC platform would be ideal, but 10 years of well rounded information security (policies to solution implementation) and outstanding communication skills would also be considered.
If you are interested - Please forward CV / Resume to This email address is being protected from spambots. You need JavaScript enabled to view it.
About FishNet Security
FishNet Security is the No. 1 provider of information security solutions that combine technology, services, support and training. Since 1996, the company has enabled clients to manage risk, meet compliance requirements and reduce costs while maximizing security effectiveness and operational efficiency. FishNet Security is committed to information security excellence and has a track record of delivering quality solutions to over 5,000 clients nationwide. For more information about FishNet Security, visit www.fishnetsecurity.com, www.facebook.com/fishnetsecurity and www.twitter.com/fishnetsecurity.
New PCI Compliance Dashboard Available - Nov 2011
Please feel free to use this “compliance dashboard” spreadsheet to sustain your PCI gap analysis exercise. It encompasses: - All PCI DSS requirements grouped by section - Guidance associated to each requirements (New) - The major observation points from the 2011 Verizon PCI Compliance report for each requirement - The PCI Glossary (New) - The participants (actors) list - The list of merchant types - The compensating controls documentation sheet (New) - The Validation Instructions for QSA/ISA for each requirement - Indication of "relevance" by merchant types (A, B, C, C-VT, D). "1" indicates that the requirement is relevant. - Priority level or milestones from the “prioritized approach” (1-6) - A column "In Place" (Yes/no/notsure) - A column "Stage of implementation (if not in place)" - A column "Estimated date for completion" - A column "Proofs/Documentation/Comment" - A column "Remediation plan" (what must be done) - A Column "Owner" (The individualor department in charge)
Javelin Study Shows Increased Credit Card Fraud Risk
Consumers, businesses, retailers, and even the media are becoming numb to news about data breaches. Not a week goes by when we don’t hear of another major breach affecting thousands or even millions of customer accounts.
Criminal hackers are getting smarter and savvier all the time, and they often have better technology than the banks and retailers tasked with protecting your data.
Time reported on a recent Javelin Strategy and Research survey in which Javelin analyzed 23 of the biggest credit card issuers’ online security practices. When companies were graded on a 100-point scale, the average result was just 59. Javelin head of security and risk analyst Phil Blank, who authored the study, explained, “The good news is issuers are doing a better job overall of resolution, but that’s the easiest thing to do. Prevention is the hardest to do but it’s got the biggest payback.”
The report also found that for a full year after your bank account information has been hacked, there is a strong chance that you will be a victim of credit card fraud. So even though you may be getting a little hardened to data breach warnings, you still need to watch your credit card statements closely. As long as you dispute unauthorized credit card charges within 60 days, federal laws limit liability to $50. Unauthorized debit card charges must be reported within two days, or liability jumps to $500.
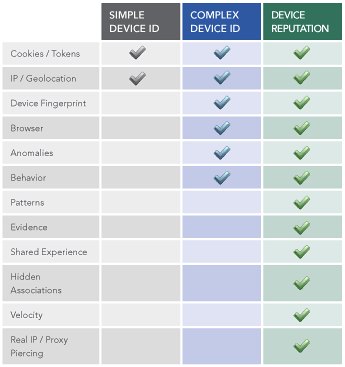
One of the FFIEC’s recommendations for financial institutions involves using complex device identification. iovation, an Oregon-based security firm, offers an advanced device identification service that incorporates real-time risk assessments, the history of fraud on linked devices (such as chargebacks, identity theft and credit application fraud) and exposes fraudsters working together to steal from online businesses.
“Complex device identification” involves the creation of a digital fingerprint based on several characteristics of the device including hardware and software configuration, Internet protocol addresses, and geolocation. Unfortunately, complex device ID by itself only increases the strength of identification; it does little to increase the efficacy of an overall anti-fraud strategy.
“Device reputation” offers all of the security measures that complex device ID does, but it also strategically incorporates velocity, anomalies, proxy busting, webs of associations (linking devices and accounts), and fraud and abuse histories. Device reputation moves from a micro to a macro view of transactions which takes into account how particular devices behave or have behaved beyond its activities with a financial institution, its usage by a current user or other users, and/or its relationship to other devices. This chart explains what is involved with each:
Leading financial institutions aren’t merely complying with the FFIEC’s security recommendations, but are going beyond it by incorporating device reputation and other authentication and anti-fraud tools into their layered security approach.
Robert Siciliano, personal security and identity theft expert contributor to iovation, discusses credit and debit card fraud on CNBC.