By Aberdeen Group
Report Description: The two fundamental purposes of this report are first, to identify the strategies, high-level tactics, internal capabilities and frameworks, technologies, and services that top performing companies are employing to realize substantial business benefits from their Enterprise Risk Management (ERM) programs. Secondly, to provide a roadmap of actionable analysis and recommendations that both companies planning to develop an ERM program for the first time, and companies seeking to augment and optimize an existing initiative can leverage to improve their performance in assessing and managing risks strategically across the enterprise.
Five Compelling Facts from the Research, Providing Actionable Benefits for Readers:
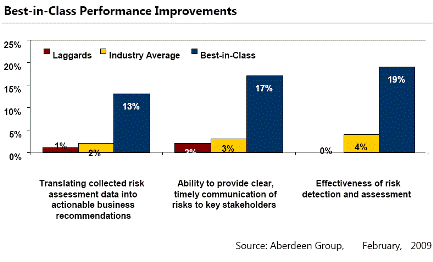
1. By focusing their strategic actions and budgetary allocations on developing and incorporating the internal capabilities, technologies, and services that facilitate embedding and ERM culture into the organizations Best-in-Class companies improved the effectiveness of risk detection and assessment by 19%.
2. As a direct result of their ERM program Best-in-Class companies improved the translation of collected risk assessment data into actionable business recommendations by 13%.
3. Establishing an enterprise-spanning consistent framework for risk management activities allowed Best-in-Class companies to experience a 9% increase in the elimination of redundant risk management activities and processes.
4. By promoting a work environment that encourages and rewards risk-centric ideas and discussions while facilitating a forum that consistently collects, tweaks, and re-focuses risk strategies Best-in-Class companies were able to improve their ability to adjust risk management processes and controls to changes in regulatory requirements and business demands by 11%.
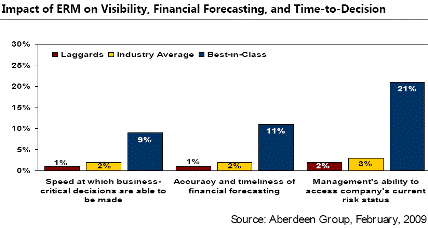
5. As a direct result of their ERM program Best-in-Class companies experienced an 10% increase in the accuracy and timeliness of financial forecasting.
Report Outakes
|
Analyst Quote ¹ Given the current global economic tightening, and the inherent difficulty in proving an ROI for effective risk management (it is almost always difficult to attach a dollar sign to something that didn't happen) a number of companies, across industries, have significantly cut or even frozen budgets for non-revenue generating business activities. Internal efforts to ensure the executive buy-in and budgetary allocations necessary to first establish, then build upon a comprehensive ERM program can be substantially aided through a two-pronged argument, essentially: (1) there a powerful business-driving, ROI-revealing value proposition flowing from effective ERM programs (although rarely is this realized right off the bat); and now (2) there is also a regulatory reason for addressing some of the foundational elements of an ERM framework. For companies without any real ERM framework in place, the "now we have to do it" element can be the impetus for cultivating a risk-based thought-process into the overall corporate mindset and leveraged as a spring-board to revamp ineffective, failed, or abandoned ERM programs. |
|
Research Quote ² Best-in-Class companies understand that the end goal of an ERM program is the embedding of a risk-aware culture into the DNA of the organization, best characterized when risk management is incorporated into every-day business activities such that it is "something that is consistently being done" rather than "something else employees have to do". Focusing their strategic actions and budgetary allocations on developing and incorporating the internal capabilities, technologies, and services that facilitate this allowed Best-in-Class companies to improve the effectiveness of risk detection and assessment by 19%. As a result, they improved the translation of that collected risk assessment data into actionable business recommendations by 13%; an average increase more than 5x greater than the Industry Average. Particularly compelling when viewed from a C-Suite perspective, these optimized risk management capabilities also enabled the Best-in-Class to improve their ability to clearly communicate a more accurate and timely view of the company's current risk status to key stakeholders. |
|
Fast Facts/Sales Quote ³ By focusing on developing risk-intelligent management capabilities, the Best-in-Class realized dramatic improvements in visibility, financial forecasting, and time-to-decision. |